Guides and reports
End-to-end encryption (E2EE) vs point-to-point encryption (P2PE) in payments
The difference between end-to-end encryption and point-to-point encryption in the context of in-person payments and how to choose which is best for your business.

Who doesn’t love a good acronym? Well hold on tight, because this article is full of them. But it’s worth it since we’ll explain the differences between end-to-end encryption (E2EE) and point-to-point encryption (P2PE) in the context of in-person payments. We’ll walk you through the workings and requirements for both so you can decide which is best for your business.
Let's dive in.
What is end-to-end encryption?
In the world of in-person or in-store payments, end-to-end encryption (E2EE to its friends) is the process of encrypting card-holder data for the entirety of the payments process. This means that, from the moment the card is tapped on or entered into a payment terminal, the data is encrypted. This sensitive data includes the shopper’s account data, such as the account number, and the track data.
How does end-to-end encryption work?
Of course different E2EE set-ups will vary slightly, but in the case of Adyen, it works because there’s only one party handling the process. The card data is encrypted at the start of the payment and doesn’t need to be unencrypted until it reaches the customer’s bank for approval. This prevents anyone in the middle from gaining access to sensitive data. It’s essentially as water-tight as it gets.
What does end-to-end encryption protect against?
E2EE protects against data breaches. There have been enough high-profile breaches in the past few years for everyone to understand the value in mitigating such risks. And, since (in the case of Adyen at least) the payment is handled by just one party; there are no weak links caused by the need to share data around. E2EE also helps to save time by reducing the workload associated with Payments Card Industry (PCI) compliance (more on that later).
What are the drawbacks of E2EE?
The most obvious drawback with an E2EE payments set-up is the all-your-eggs-in-one-basket concern. Of course if you have one partner handling the entire payment flow, including the data security, you want to be sure they’re solid. Fortunately, payments providers like Adyen are subject to the strictest possible regulations. The Payments Card Industry Security Standards Council’s (PCI SSC) is an independent organisation guarding the security of online and in-store payments and Adyen is a fully validated solution.

What is point-to-point encryption (P2PE)?
As an intro to P2PE, cast your mind back to 2011. Will and Kate were newly hitched and Azerbaijan had just won the Eurovision Song Contest. There was also a massive fraud attack on a major gaming network in which names, addresses, and payment data belonging to 77 million user accounts were breached. In a ‘never again’ moment, the PCI SSC launched its P2PE program.
Like E2EE, P2PE is an encryption method in which the payment data is encrypted from the point the customer shares it to the point it reaches the card acquirer. In the case of P2PE however, it also puts the onus back on the businesses in terms of validating the secure handling of terminals before installation, when in use, and at the end of a terminal’s life.
How does point-to-point encryption work?
The P2P in P2PE stands for point-to-point. The sensitive account data is protected from when the payment card is presented at the payment terminal until it reaches the acquirer. In case of an attempted breach at any point, the E in P2PE, encryption, means there is no impact to the customer, or their data.
The benefits of point-to-point encryption
In addition to protecting your customers’ sensitive card data, P2PE cuts down the scope of PCI compliance. To meet PCI compliance, businesses must complete a questionnaire, also known as a Self Assessment Questionnaire (SAQ). This a checklist that tells your acquirer you’re taking the appropriate security measures to keep data safe and meet compliance.
If you don’t have P2PE in place (and you’re not being taken care of by an E2EE provider like Adyen), you’ll have up to 12 requirements and 329 questions to answer every year. If you do have P2PE, the requirements drop to three and the questions to 35.
What are the drawbacks of point-to-point encryption?
The main drawback of P2PE is that you’re still subject to a degree of compliance workload, especially when it comes to safeguarding your terminals. For example, you’re required to adhere to a document called the P2PE Instruction Manual (PIM), which is provided by your solution provider.
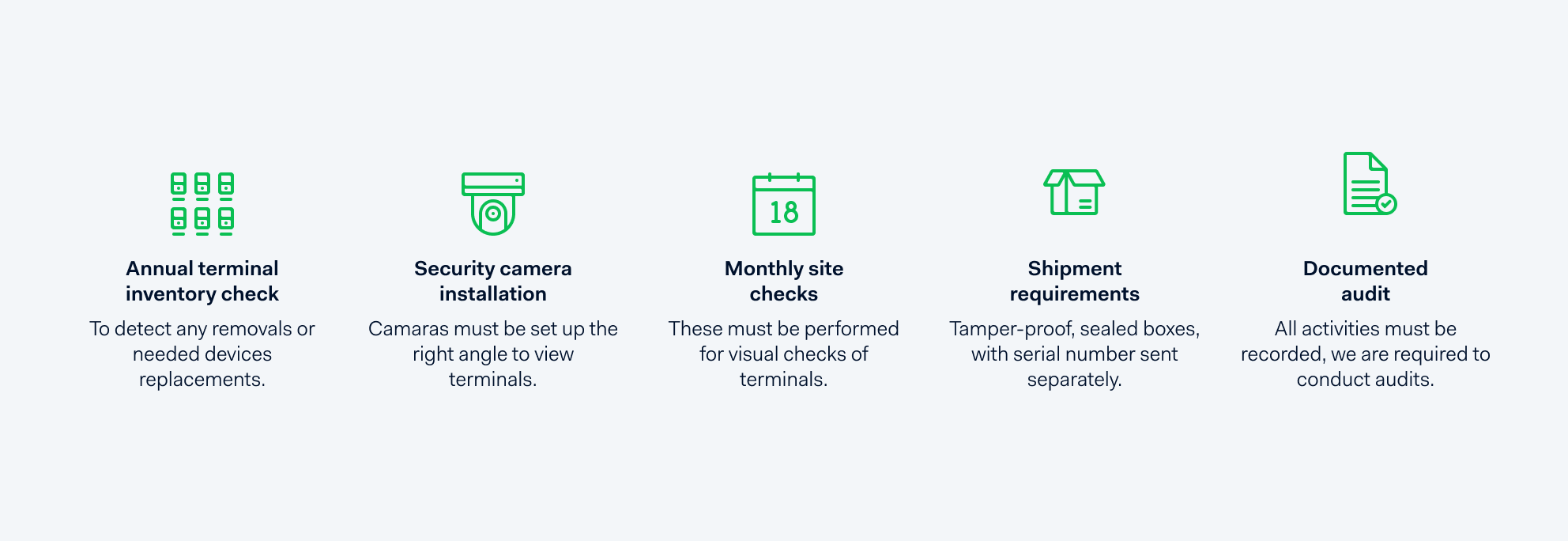
In comparison, with Adyen’s E2EE solution, we don’t require any of the above. The only item you’ll see is the tamper-proof, sealed boxes we send our terminals in.
Which type of encryption do I need?
When it comes to choosing the right encryption for your business, it ultimately boils down to the level of security you need as well as how your business manages its resources.
First off, it’s worth considering the requirements of that Self Assessment Questionnaire. Below illustrates the difference between each level of encryption.
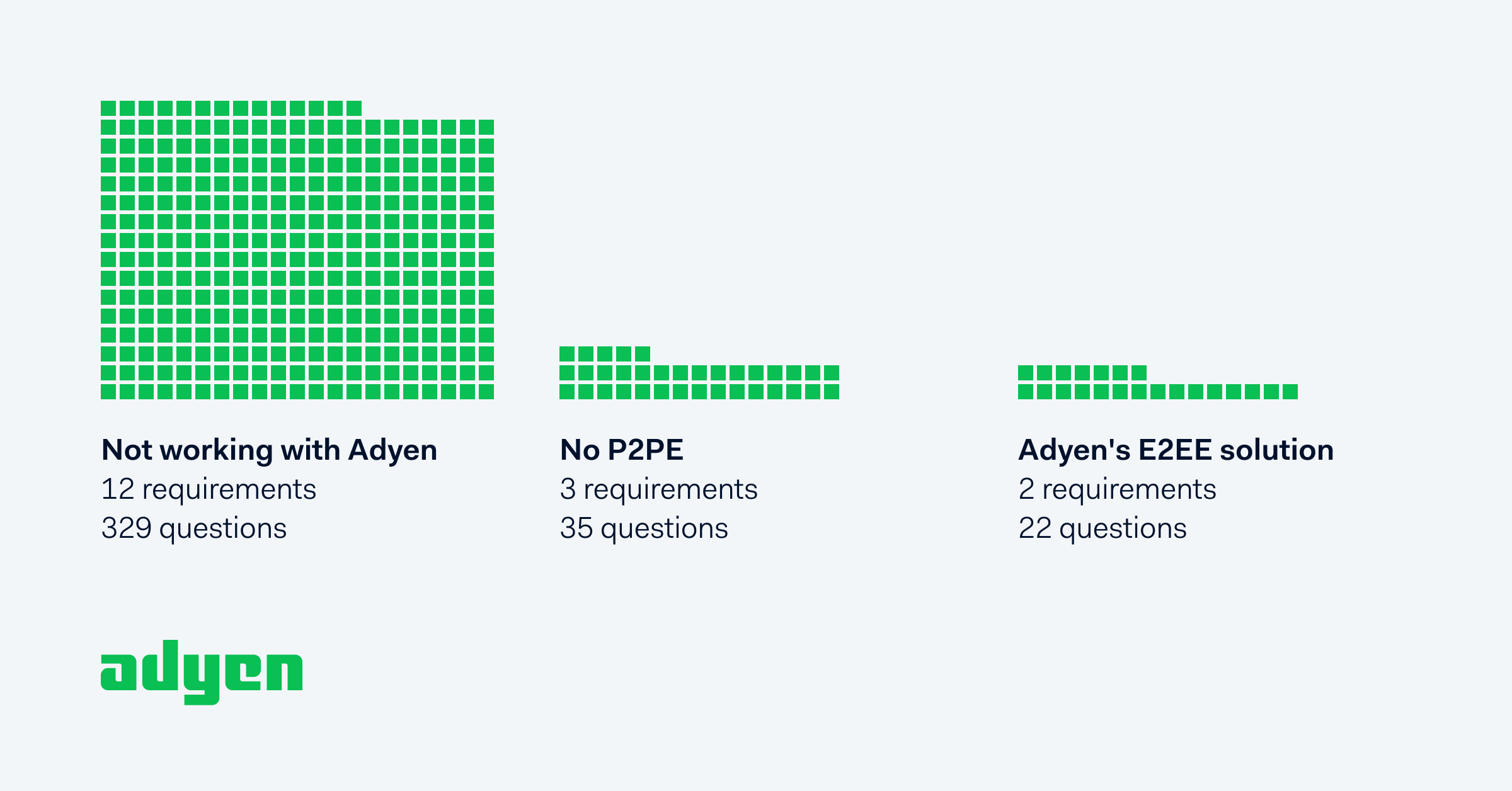
As you can see, the workload drops significantly when you have P2PE and even more so with our E2EE solution.
Why E2EE?
We believe in high-quality data security, without all the extra work. This is why we built an E2EE payment solution in a way that ensures the best possible data security. More agile, decentralised businesses will find E2EE more efficient. Examples of these could be enterprises that don’t need to centralise operational control, such as franchises, or scale-ups with smaller teams and aggressive roadmaps.

Why P2PE?
Larger, more heavily-resourced businesses with an aversion to risk prefer the P2PE solution as it gives them an added layer of control around the physical handling of terminals. They’re likely willing to pay per POS terminal for the added security it provides. They will also spend more time and human resources to maintain the PIM.

Example questions include:
- The make and model of the device
- Location of device (for example, the address of the site or facility where the device is located)
- Device serial number or another method of unique identification
What Adyen offers
Adyen is a P2PE-validated solution provider, which complements our existing E2EE solution. By using P2PE with us you still benefit from working with a single partner but there’s a tradeoff between the added value of external validation, and increased operational effort. For that reason, we find many of our customers prefer to stick with just our E2EE solution. But that’s up to you. Either way, we have you covered.
Want to learn more?
Find out how Adyen can help your business with all your payment encryption needs.
Speak to a payments expert